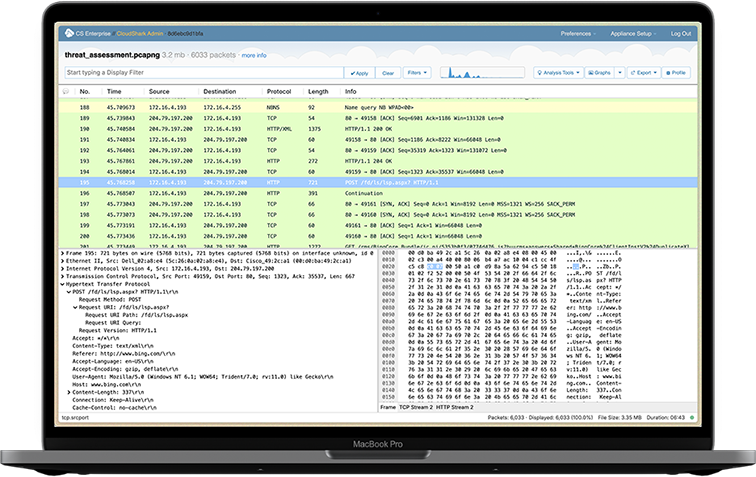
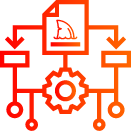
Solve network and cybersecurity problems faster with a complete solution that drastically improves operational efficiency at scale.
CloudShark® Enterprise delivers efficient, scalable packet analysis for today’s enterprise networks — where multi-gigabyte captures, distributed teams, and high-speed links are the norm.
Standardized PCAP Workflow
UPLOAD AND IMPORT
Integrate CloudShark Enterprise’s upload API into other tools anywhere in your network, or let users drag and drop directly using their browser.
SPLIT LARGE FILES AND SEARCH WITHIN PCAPs
Open, split, and index large captures. Then use Deep Search with Wireshark display filters to pinpoint anything from IPs, DNS queries, errors, and more across every file in your repository.
LEVERAGE ANALYSIS PROFILES
Build profiles that can be updated globally to analyze specific problems and help experts and entry-level technicians work together while creating standard operating procedures around problem solving.
SHARE EASILY AND REDUCE BANDWIDTH
All your analysis is saved and can be shared with a URL. Instead of downloading large pcaps and reproducing analysis steps each time someone opens a file, link directly to it for them to see.
Work with Massive Capture Files
UPLOAD AND STORE LARGE CAPTURES
Add even multi-gigabyte files directly into CloudShark Enterprise. No more waiting, crashing, or guessing which chunk of the data matters.
SPLIT
Divide large captures into smaller, manageable segments using built-in tools — by time, by packet count, or by bandwidth slice. Each split file is searchable without losing fidelity.
DEEP SEARCH
Instantly search across every split file using standard Wireshark display filters. Find exactly where anomalies occur — IPs, ports, DNS names, errors — across your entire repository of captures.
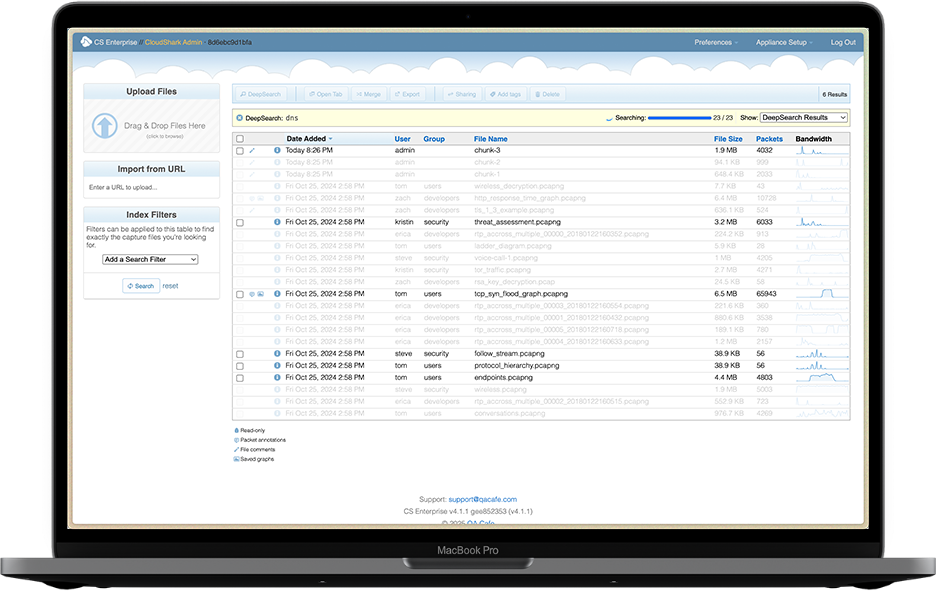
Streamlined Deployment & Automation
DEPLOY ANYWHERE WITH ONE LICENSE
CloudShark Enterprise’s simple license lets you delf-deploy unlimited instances with unlimited seats wherever and whenever they are needed. Deploy per-region for compliance, deploy per-customer for support, or deploy and tear down instances for specific issues that require secure engagement.
WORKS IN DOCKER FOR CONTAINERIZED ENVIRONMENTS
CloudShark Enterprise is easily deployed as an OVA or in Docker environments as part of your network automation and orchestration.
INTEGRATE WITH EXISTING TOOLS AND AUTOMATION
Whether integrating with ticketing systems, SIEM platforms, or capture appliances, the CloudShark Enterprise API gives you the power to make packet capture analysis a seamless part of your operational pipeline.
Watch video
Looking for integration/OEM opportunities?Add secure integrated packet analysis to your cloud-managed networking or cybersecurity solution
Packet Viewer is the power behind CloudShark and easily integrates directly into your existing solution and brand, enhancing your product with a familiar and comprehensive packet analysis experience.
Learn moreConnecting the dotsDiscover how CloudShark is helping our customers improve network troubleshooting & investigation
Webinars
Webinar - How TCP reassembly quirks can be used to hide attacks
February 23, 2021 · 1 min readWhen analyzing network traffic, we rely on our tools to show us how a TCP stream was reassembled or to give us a list of HTTP websites accessed in a pcap file.
Articles
Keeping Packet Data Local: Deploying Your Analysis Tools Regionally
June 09, 2025If your team relies on packet analysis to secure and troubleshoot networks, you already know the stakes: Compliance with data privacy laws isn’t optional. How do you maintain visibility into critical packet data without letting it cross geographic boundaries?
Articles
Analyze Where the Packets Are - Tips for Global SOCs and MSSPs
July 12, 2025Here’s the problem: The packets you need are there. You are here. And between you and the data are slow transfers, siloed systems, and a growing backlog of other environments waiting for attention. Here's how to get around it with the right packet analysis tools.