Articles
Digital Forensic Investigation Using CloudShark Threat Assessment
Network packet captures contain the hard evidence you need when performing cybersecurity Digital Forensics and Incident Response (DFIR). They are especially powerful when applied to an intrusion detection system (IDS), like Suricata, which can operate on packet captures as if they were live traffic.
Applying threat rules to packet captures
Suspicious network activity is often identified using “threat signatures” which generate an alert based on predefined rules, collectively known as a “ruleset”. The alert includes details such as the source and destination IP addresses, timestamps, and the specific signature that triggered the alert.
“There’s no magic to Suricata and other forensic tools on their own - having a great visualization that lets us pivot from an alert to the PCAPs was a critical point for us.” - Jeremy Brown, Trinity Cyber
On their own, these alerts are difficult to visualize. CloudShark uses a “ladder diagram” view to provide some additional context to each alert, including the endpoints that generated and received the traffic and directionality.
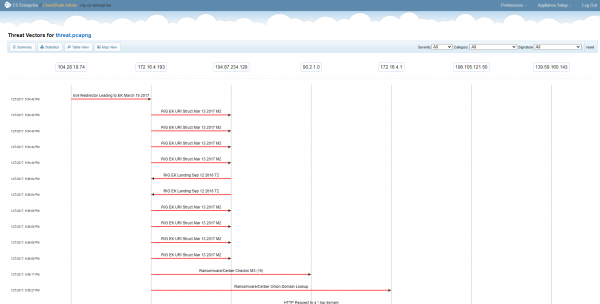
This is a good starting point for many investigations. Each of the above alerts can be expanded to show the details of the alert, with easy access to any further information. The real power, however, comes from the ability to pivot directly to the recorded network data associated with the alert.
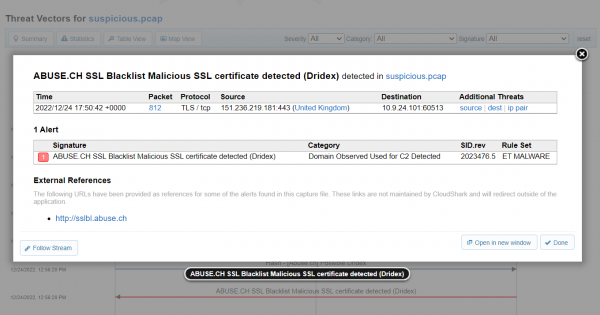
Why pivot to the packets?
In a traditional security analysis workflow, security analysts often need to manually correlate alerts with packet data, which can be time-consuming and prone to errors. In CloudShark, you can go to the exact packet that triggered the alert, or to the entire conversation stream related to it by clicking “follow stream”, then “show only this stream”. However you choose to start looking, having full access to switch between your alert view and packet view, the ability to pivot directly to the packets provides several benefits:
- Detailed insight: Network packets provide granular information about the communication between different devices in a network. By examining the packets associated with an alert, security analysts can gain valuable insights into the specifics of a security incident, such as the protocols and ports used, the payload content, and the sequence of events that led to the alert. This detailed information is crucial for understanding the nature and scope of a security threat and developing an appropriate response strategy.
- Faster investigation: Pivoting directly to the relevant packets helps streamline the investigation process by eliminating the need for manual data correlation. Security analysts can quickly navigate through the packet data and focus on analyzing the critical aspects of the incident. By applying annotations to captures, applying agreed-upon profiles, and sharing the same capture by CloudShark URL, analysts can avoid repeating work and greatly accelerate their investigation.
- Enhanced detection capabilities: Pivoting to the packets allows security analysts to identify patterns, anomalies, and potential indicators of compromise (IoCs) that might not be apparent from the alert data alone. Combined with CloudShark DeepSearch, analysts can also use IoCs as search terms to uncover the same behavior in other packet captures to see if the same attack happened before, or again.
- Reduced False Positives: By closely examining the packet data associated with an alert, security analysts can more effectively distinguish between genuine security incidents and false positives. This ability to accurately identify true threats helps security teams prioritize their efforts and allocate resources more efficiently, resulting in a more effective security posture.
- Accurate root cause analysis: Examining the packets associated with an alert enables security analysts to identify the root cause of an incident with a higher degree of accuracy. By understanding the exact sequence of events and the specific factors that triggered the alert, analysts can develop targeted mitigation strategies and make better-informed decisions about how to remediate vulnerabilities and improve network defenses.
Adding packet captures to your DFIR strategy
As cyber threats evolve in complexity, including packet captures in your DFIR strategy becomes increasingly important for maintaining a strong security posture and ensuring a swift and effective response to potential threats. They add a vital layer of granularity and depth to your security investigations that give analysts a comprehensive understanding of the events that led to an incident and enables them to accurately identify root causes and develop targeted mitigation strategies.
You can read more about how to use CloudShark in your overall incident response in these articles:
- 5 tips to improve incident response using packet captures
- Faster network and security pcap analysis with Zeek logs
- PCAP Collaboration Tips for NetSecOps Teams