Articles
How to get security traffic analysis insights during testing and why they're important
4 min read
Securing home/soho routers and WiFi network devices has become the most important topic for vendors and service providers. Ensuring network devices behave as intended, before they are deployed, is critical to avoiding unnecessary costs, avoiding brand damage, and guaranteeing a quality end-user experience.
QA Cafe’s CDRouter Security add-on is built specifically to tackle these challenges. Here is an overview of these features and how they will help you improve your product security testing.
Security traffic analysis for home gateways
Security testing of home gateways is a broad problem with many facets. In addition to actively testing known vulnerabilities, port scanning, and exercising security features, monitoring your products’ live network behavior can show security flaws and outline best practices critical to product quality, reducing future design changes or compromised customer networks.
Performing security traffic analysis during testing lets you observe the behavior of your devices under test outside of the known and predictable test traffic. By monitoring the traffic a device sends to the Internet or to specific cloud resources, you can receive alerts for traffic that is suspicious, surprising, or that goes against known deployment policy guidelines.
What can you monitor during testing?
Security traffic analysis separates traffic that is destined for CDRouter’s simulated network endpoints from traffic that would be sent to other network destinations.
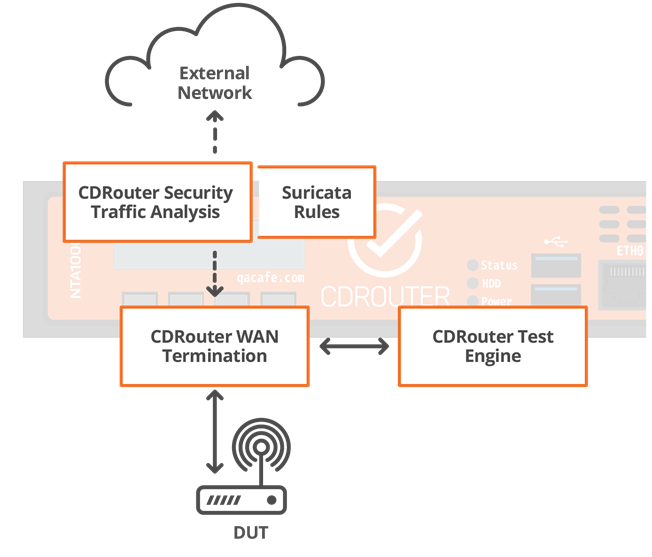
For example, many devices today perform a network connectivity “sanity check” by attempting to connect to known sites like Facebook, Google, etc. This traffic bound for the Internet is monitored, captured, and analyzed by CDRouter using “rules” written in the format of the open-source IDS platform known as Suricata.
What is a rule and a rule set?
An IDS rule specifies certain properties, called “signatures”, to watch for when analyzing traffic. A collection of these rules is called a “rule set”. There are open-source rule sets that have been curated by the security industry, like the ET (Emerging Threats) Open rule set, that are periodically updated to include the latest malware signatures.
In addition to Emerging Threats rule sets, CDRouter’s security traffic analysis will include a rule set built and maintained by QA Cafe. This will contain rules that focus on security best practices for home/soho routers and WiFi network devices.
Can I make my own rules?
Yes! There is a standardized syntax for Suricata rules and doing so can be very powerful for your testing. In addition to writing your own security checks, you could write rules that flag certain policy behavior. For example, a device with a hard-coded ACS that has its ACS URL changed should be checked to ensure that the new firmware does not communicate with the old server.
How is this different from a test case?
These rules are applied passively to the network traffic that occurs outside of the CDRouter closed-loop test procedures. As such, they do not have “pass/fail” metrics associated with them. Instead, your test results will show a set of alerts that were triggered during testing for you to investigate further.
These alerts work alongside your test packages. Often, we’ve seen alerts triggered traffic that was sent by the device due to our simulated user activity like web traffic, DNS queries, etc. This lets you get a full picture of your device’s real-world behavior!
How is this important?
There are a number of use cases for security traffic monitoring of devices under test. Here are a few we have encountered after discussions with first users:
- Testing a vendor device for bad behavior before deployment
- Testing a compromised device that has been isolated for lab testing
- Ensuring that provider-specified policies are met
- Regression testing your devices after a security fix
Learning more
The CDRouter Security add-on adds these features to our industry standard automated test platform. You can watch an in-depth webinar for more.
Ready to secure your networking devices before they’re deployed? Request a demo today!