Articles
Captures and Analysis of the QUANTUMINSERT Attack
1 min read
We now know a lot about the NSA’s various techniques in its QUANTUM program. One of the most prolific (and sneaky) of these attacks is the “QUANTUMINSERT”, which exploits a long-known TCP vulnerability that will cause, effectively, a redirect to a malicious resource. It’s tricky, since it requires careful timing; the spoofed packet needs to arrive before the expected packet.
One of our most engaging customers, Fox-IT, is an active team of hackers, programmers, and cybersecurity experts that provides innovative solutions for government, defense, law enforcement, critical infrastructure, banking, and commercial enterprise clients worldwide. They have analyzed the QUANTUM insert attack and have made a detailed explanation of how to simulate and detect the attack.
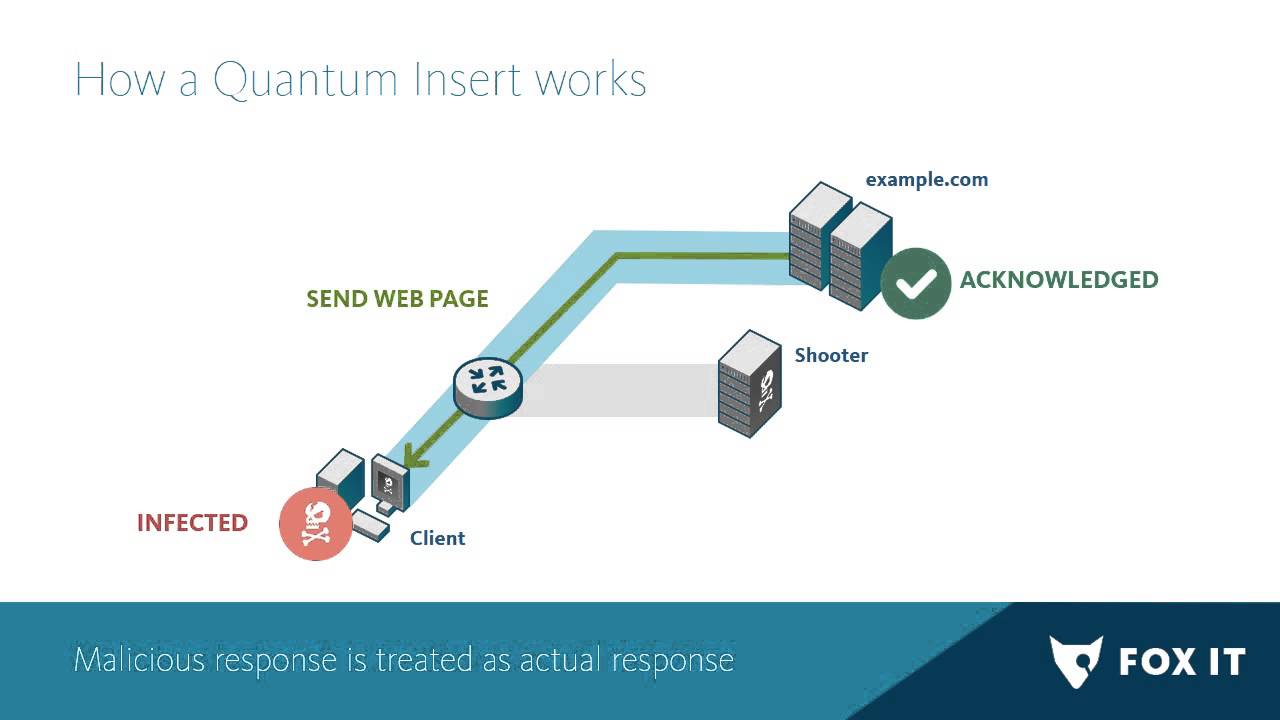
Annotated Captures
Fox-IT has been kind enough to make a set of annoated captures that show the attack in action. You can see several examples below, with CloudShark’s annotations that were automatically imported from Fox-IT’s pcapng files.
An archive of these files is on GitHub.
- qi_internet_SYNACK_curl_jsonip.pcapng
- qi_local_GET_slashdot_redirect.pcapng
- qi_local_SYNACK_curl_jsonip.pcapng
- qi_local_SYNACK_imgur_qdp.pcapng
- qi_local_SYNACK_linkedin_redirect.pcapng
- qi_local_SYNACK_putty_dl.pcapng
- qi_local_SYNACK_slashdot_redirect.pcapng
This is excellent analysis, we’re glad to help Fox-IT show them to the network community.
Want articles like this delivered right to your inbox?
No spam, just good networking