Articles
Securely troubleshoot remote systems with Couchdrop and CloudShark
3 min read
Couchdrop.io is a secure cloud storage service that lets you use SCP to manipulate your data assets. They’ve integrated with cloud storage giants like Dropbox, Google Drive, and AWS-S3. With their CloudShark integration, you can make use of custom scripts or interaction with remote servers that have packet capture capability to instantly and securely push network traces to CloudShark, analyzing them without ever leaving your browser.
Working with logs, captures, and other remote data
Couchdrop is a cloud-based SCP server that can be used for any kind of data, but it has some particular advantages when troubleshooting remote servers, firewalls, and other systems.
- Flexibility in handling files – Let’s say you’re dealing with an incident and need log files, configuration details, and packet captures together in order to get a full picture of what’s going on. Couchdrop is a repository and is integrated with all manner of other storage services, letting you send your log files to Couchdrop (or another location) and your captures to CloudShark all using the same tool.
- One line to rule them all – Sending files through Couchdrop is a single command that is fast, reliable, and can be easily integrated into scripts built to scrape necessary data from remote systems.
- Commonly deployed – SCP (and its foundational protocol, SSH) is widely supported by a large number of devices, meaning there’s usually no need to install further packages or build additional scripts to get it to work.
- Perfect for CloudShark online accounts – Our Enterprise users who want to make use of SCP can do so using an assigned directory and our auto-import feature. CloudShark Online can get the same benefits of using SCP with Couchdrop!
How does it work?
First sign up for a Couchdrop.io account, and a CloudShark account if you don’t already have one. Then, follow the steps the Couchdrop team has described to set up the CloudShark integration. Capture traffic (using tcpdump, dumpcap, tshark, or your firewall’s internal capture tools), and when the file is available, push it to CloudShark through Couchdrop with a command like this:
scp filename.pcap couchdrop-username@couchdrop.io:/cloudshark
You’ll find your packet capture sitting in your CloudShark account ready for analysis!
Example
Here we are taking a packet capture on the ‘ens38’ interface for both port 67 and 68 (DHCP) and transferring the output into the “packetcapture001.pcap” file.
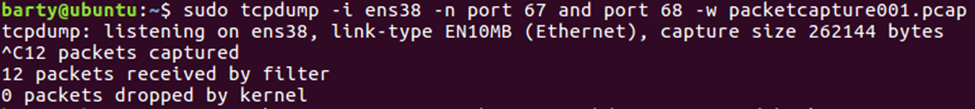
Once we have the packet capture we are uploading here directly to our CloudShark account.
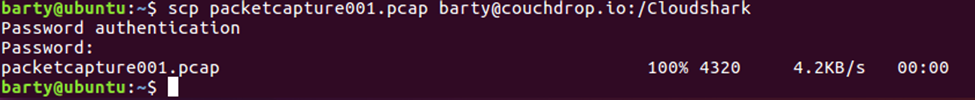
Once there, you’ll see the capture in your repository on CloudShark
Where you can start your analysis right away.
It’s that easy! Check out Coudrop.io and let us know what you think!
Want articles like this delivered right to your inbox?
No spam, just good networking